
Just before last Christmas, in a first-of-a-kind case, JPMorgan was fined $200M for employees using non-sanctioned applications for communicating about financial strategy. No mention of insider trading, naked shorting, or any malevolence. Just employees circumventing regulation using, well, Shadow IT. Not because they tried to obfuscate or hide anything, simply because it was a convenient tool that they preferred over any other sanctioned products (which JPMorgan certainly has quite a few of.)
Visibility into unknown and unsanctioned applications has been required by regulators and also recommended by the Center for Internet Security community for a long time. Yet it seems like new and better approaches are still in demand. Gartner has identified External Attack Surface Management, Digital Supply Chain Risk, and Identity Threat Detection as the top three trends to focus on in 2022, all of which are closely intertwined with Shadow IT.
“Shadow IDs,” or in other words, unmanaged employee identities and accounts in third-party services are often created using a simple email-and-password-based registration. CASBs and corporate SSO solutions are limited to a few sanctioned applications and are not widely adopted on most websites and services either. This means, that a large part of an organization’s external surface –as well as its user identities– may be completely invisible.

Above all, these Shadow IDs remain unmanaged even after employees leave the organization. This may result in unauthorized access to sensitive customer data or other cloud-based services. Employee-created, but business-related identities are unseen for most IDM/IAM tools also. The graveyard of forgotten accounts belonging to ex-employees or abandoned applications is growing every day, to infinity.
And sometimes, the dead rise from their graves, as with the Joint Commission On Public Ethics, whose legacy system was breached this year, even though it’s been out of use since 2015. They rightfully notified their legacy users because they understand that password reuse may stretch over several years, and according to Verizon, stolen credentials are still the top contributor to all sorts of breaches and attacks. So when Shadow IDs are left behind, they create an everlasting risk unseen and unmanaged by anyone.
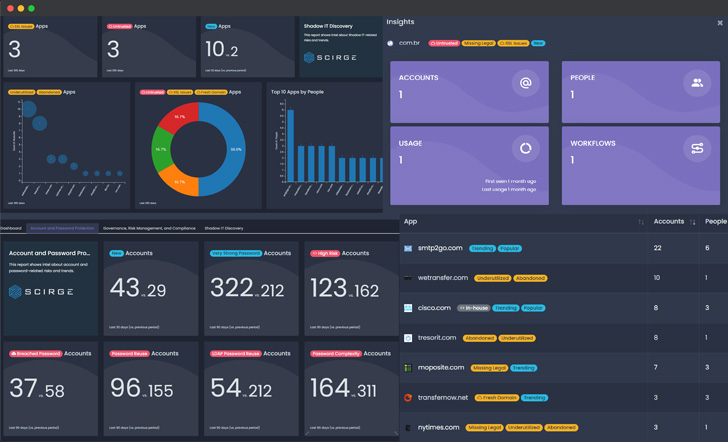
How to Report on Shadow IT and Shadow IDs?
Unfortunately, network monitoring misses the mark, as those tools are designed to filter malicious traffic, provide data leakage protection and create category-based rules for browsing. However, they are completely blind to actual logins, and thus cannot differentiate browsing, private accounts, and corporate application signups, (or phishing sites for that matter). To discover and manage Shadow IDs and Shadow IT, there needs to be application and account-level monitoring in place, that can create a trusted, global source of truth across the organization.
Discovering these assets via monitoring business-related credential usage on any website enables a unified view of unsanctioned or unwanted applications. Inventories of apps and accounts provide visibility of the true scope of external services and identities used across the organization. Also, they allow the reviewing of third-party providers about their policies, security and authentication measures, and how they are managing and maintaining your data.
It is impossible to properly categorize all of the quarter-million new domains that are registered each day across the globe, so monitoring those that show up on our endpoints is the right approach. As a side-effect, revealing logins on suspicious or new apps will give visibility into successful phishing attacks that were not prevented on a gateway or client-side, and where employees gave away important credentials.
Scirge is a browser-based tool that provides complete visibility into Shadow IDs and Shadow IT, password hygiene for corporate and third-party business web accounts, and even real-time employee education and awareness. And it also has a completely free version for auditing your cloud footprint, so you can get an immediate view of the extent of Shadow IT amongst your employees.













